What are SHA and MD5 and why should you care?

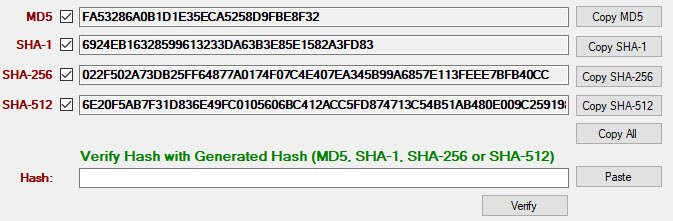
Well, to answer the first question, SHA and MD5 are cryptographic algorithms that take an input (in this case a file) and create an output based on the input. It is very hard to emulate that same output without the exact same piece of input. Does that clear it up? An easier way to think about it is this: you take file, run it through a SHA algorithm and it spits out a result that may look something like this:
61bc17ee83ffa12e674af35503181bb336e943ccefac90805807f4bf0137e4b2 (this is a SHA 256 hash)
Only that one specific file will create this unique hash code, no other file will create that exact same hash. Think of it like a unique signature that’s perfect every time.
So why should you care?
Well, the answer is, unless you’re an advanced user that downloads files from open source or other non-corporate websites, then you’ll probably never have to worry about it. This is more of an advanced tool that people can use to verify the file they just downloaded is the file it’s supposed to be.
So for example, I download a piece of software from a website. Right next to the download button, I spot a SHA-256 hash similar to the one posted above. After I download the file, I use the MD5-SHA checksum utility to quickly check that the piece of software I downloaded is what it’s supposed to be. If the SHA hash didn’t match, I’d know that I’ve got something different and I would know not to install it. (Actually what I should then do is delete it and contact the website owner).
MD5 is dead
It’s important to note that MD5 is old, weak, and has been broken. That means MD5 hashes can be faked and shouldn’t be trusted. If it’s all you’ve got, you can still verify it, but just know that it doesn’t mean your safe.
Secure Hash Algorithm (SHA)
SHA is actually a family of hashing algorithms. There’s SHA-1 (also broken), SHA-256, SHA-384, and SHA-512. As the numbers get higher, so does the length of the hashes (or signatures). The more complex the algorithm, the harder it is to fake.
It’s important to understand, nothing is being encrypted here. You’re only checking the signature of the file you downloaded, matches the signature the website posted for you to check against. I’ve posted some how to videos to help explain.
